As cybercrime costs continue to soar, law enforcement agencies are increasingly turning to OSINT to proactively detect threats, investigate attacks and prevent costly breaches before they occur.
The cost of cybercrime is increasing year after year. According to Cybersecurity Ventures, the global annual cost of cybercrime is projected to reach more than $12 trillion by 2031. This massive number is even expected to increase further as the world digitalizes all aspects of life and business.
Preventing and investigating cybercrime after it occurs also incurs massive amounts of money. For instance, the cost of a single data breach has reached $4.88 million, according to IBM data breach report. This number includes the costs of hiring experienced digital forensics inspectors and acquiring other services from different third-party providers to execute the investigation. All these costs participate in one aspect or another, making working in today's complex threat landscape costly and dangerous.
As digital technologies open numerous opportunities for attackers to widen their attack surface, they also provide important information for defenders to halt cyberattacks even before they occur. Open source intelligence, which is information collected from public sources, mainly digital sources, has become an indispensable tool for law enforcement to solve and mitigate cybercrime. Security teams leverage OSINT techniques to monitor dark web forums where stolen credentials circulate, track emerging exploit kits advertised on underground marketplaces, and identify adversary IT infrastructure before attacks manifest. Numerous financial institutions now deploy OSINT capabilities to detect data leakage from third-party vendors, thereby averting potential breaches that would otherwise cost millions.
Key OSINT sources for law enforcement
OSINT has become an essential element in law enforcement agencies' arsenals. For instance, it enables them to gather evidence and intelligence from publicly available sources in real-time with minimal effort and costs. Here are some key OSINT sources and examples of how they can be utilized in law enforcement investigations:
Social media platforms
The number of social media users is increasing every second. A recent statistic by Datareportal predicts that there are almost 5.31 billion users worldwide across the different social media platforms (e.g., Facebook, Instagram, X and LinkedIn). Users on social media post all types of content, such as photos, videos, and text post, in addition to check-ins that reveal their geographical location. Most information available on social media can be accessed freely without prior permission, and it reveals important information about the subject entity, such as their lifestyle, wealth, health condition, shapes and their properties (e.g., houses, cars and other luxury items), among other things. Law enforcement can monitor these platforms for evidence related to criminal activities, such as drug trafficking or threats against public officials.
Search engines
Search engines are not a repository of data in their own, they provide access to other resources that cannot be found without using search engines. OSINT gatherers commonly utilize advanced Google search techniques, called Google Dorks, to find information buried in deep resources that cannot be found using conventional search engines.
For example, here are some Google Dorks to find specific information that typical search queries cannot find:
- site:authentic8.com filetype:doc OR filetype:docx OR filetype:PDF | This search query searches for Microsoft Word and Acrobat documents within the Authentic8.com website. These might include drafts, reports, or other internal communications that may contain sensitive information (see Figure 1).
- site:authentic8.com inurl:admin OR inurl:login OR inurl:panel | This query searches for URLs on the site that contain words like "admin," "login," or "panel." These are often associated with administrative or login portals, which, if misconfigured, could reveal access points to attackers' websites.
- site:authentic8.com intitle:"index of /" | This searches for pages with the title "index of /" on the authentic8.com domain. These are directory listings on web servers, which can sometimes expose the file structure and contents of directories that are not intended to be public.
- site:authentic8.com inurl:config OR inurl:backup | This dork looks for URLs containing "config" or "backup," which might point to configuration files or backup archives that could inadvertently expose sensitive settings.
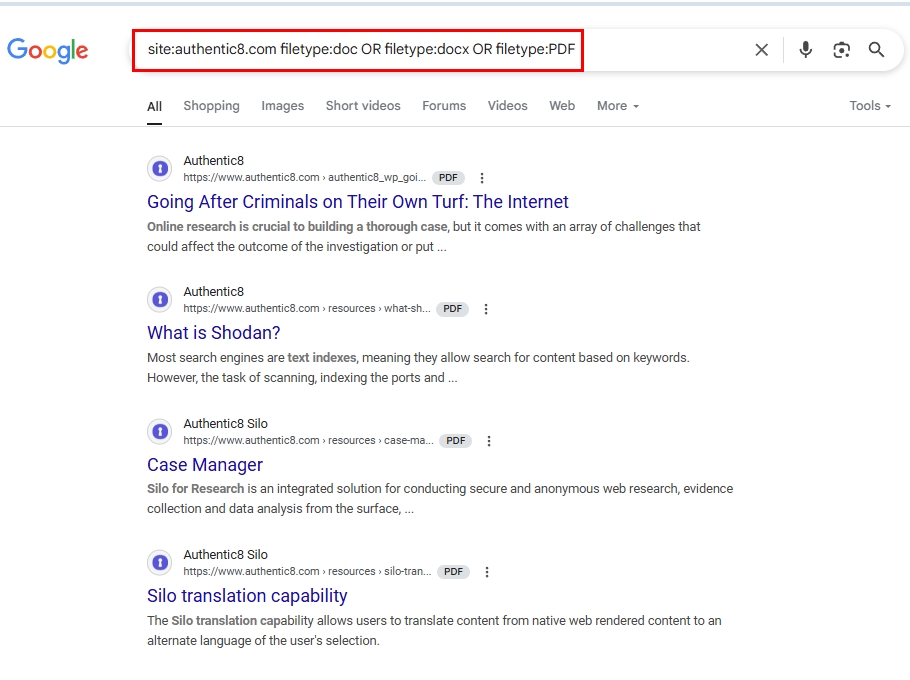
Figure 1 - Using Google Dorks to find sensitive and buried documents that typical search techniques cannot find
Public records and government databases
Law enforcement can get a plethora of information from public records and databases, such as:
- Property records: These records reveal ownership details, property history, and associated addresses. Such information provides insights into a target (both individual and organizations) financial status or past activities. In the US, the "Public Records Online Directory" provides access to a database of Tax Assessors', Treasurers' and Recorders' offices.
- Criminal records: Accessing criminal history can help in assessing potential risks associated with individuals. This information is vital for law enforcement and for private investigators when conducting background checks or assessing threats against someone. In the USA, we can use Public Access to Court Electronic Records (PACER)
- Court documents: Legal filings, including civil and criminal cases, can provide context about disputes, legal obligations, and the history of interactions with the legal system. This data is useful for understanding the legal landscape surrounding a person or organization.
- Business filings: Information about business registrations (e.g., Opencorporates, UK companies house), licenses, and corporate structures can help law enforcement understand the operational framework of target companies, including details about ownership and management.
- Government databases: These can include a variety of records, such as voter registrations, vital records (e.g., USA Vital Records website), professional licenses, and more, which can be used to verify identities and affiliations.
- Historical data: Many public records databases offer access to historical data, enabling analysts to track changes over time, such as shifts in property ownership or changes in criminal behavior.
Geospatial intelligence
When it comes to investigations, whether it is a crime scene, a suspicious location, or an area of operational interest, geospatial intelligence (GEOINT) comes into play. It is not just about maps; it is about layering data, patterns, and movement to uncover what is hidden in plain sight.
GEOINT is very important for law enforcement for the following reasons:
- Pinpoint accuracy: Exact coordinates are critical in investigations. For example, giving GPS coordinates (at 48.8574° N, 2.3555° E) rather than saying "near the park". Whether it is a suspect's last known position, the path of a fleeing vehicle, or the line of sight between buildings, precision turns hunches into actionable intelligence.
- Pattern recognition: For example, a vehicle circling the same street every Thursday, or foot traffic spiking in restricted zones after midnight? GEOINT algorithms crunch thousands of data points to flag the anomalies law enforcement may miss.
- Cross-referencing data: Satellite imagery confirms the terrain. Traffic cams verify vehicle type. Geotagged posts place individuals on the map. Adding witness reports, the puzzle pieces start to lock into place. GEOINT will help law enforcement not just collect, but also correlate information.
Darknet
The darknet is a part of the internet that conventional search engines cannot index. It requires specific software to access, such as Tor (download Tor Browser to access Tor darknet). Darknet, such as the Tor darknet, serve as a significant source of OSINT for law enforcement. Here is some information law enforcement can get from the darknet:
- Illicit marketplaces: Many darknet marketplaces facilitate selling and promoting illegal goods and services, such as drugs, firearms and fake government documents (see Figure 2). Law enforcement officers monitor these platforms to gather intelligence and try to identify the sellers and buyers of illegal goods.
- Communication platforms: The darknet hosts different programs and platforms that facilitate secure chat between cybercriminals. Law enforcement can monitor these platforms to get valuable insights into criminal networks and future attack plans.
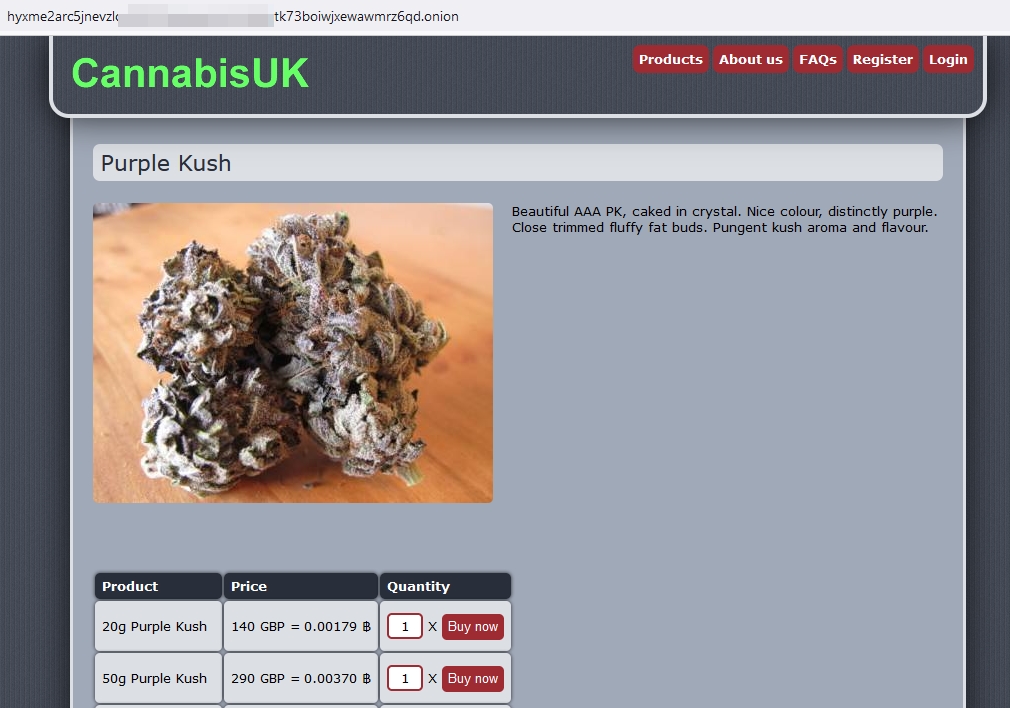
Figure 2 - An Onion website selling drugs using Bitcoin (advertised on the Tor darknet)
There are also dedicated websites that provide a directory listing of different OSINT tools and online services. My OSINT portal is a good example of such directory listings, available at http://www.osint.link(see Figure 3).
Figure 3 - OSINT.link provides links to a vast array of OSINT tools and online resources
How does law enforcement use OSINT to prevent crimes?
OSINT is not only a valuable tool for executing investigations; it can also be used effectively as a proactive measure to prevent crimes before they occur. By monitoring publicly available data across diverse sources, law enforcement can detect threats, track suspicious people, and disrupt criminal activity in real-time. Here is how they do it:
- Monitoring social media for threats – law enforcement officers monitor social media platforms continually to detect threats, such as mass shooting warnings, bomb threats, and gang violence. It is common for criminals to brag about their illegal activities and social media platforms, such as Facebook and TikTok, are the preferred location for doing this. Artificial intelligence (AI) technology can be used in this context to continually scan all social media platforms for specific keywords or high-risk posts (e.g., threats against schools, public figures) and inform law enforcement to take immediate action. Within this context, Google Alerts can be used to notify us when a specific word or phrase is mentioned anywhere online.
- Tracking organized criminal groups – For instance, encrypted internet messaging applications such as Telegram and Signal in addition to dark web forums can be monitored for chats mentioning drug, weapons and human trafficking. This allows law enforcement to disrupt illegal plans before they occur.
- Stop human trafficking activities – Cryptocurrency transactions such as Ethereum and Bitcoin can help detect human trafficking activities and trace criminals dealing with illegal goods and services. For instance, by analyzing blockchain patterns associated with known trafficking operations, investigators can identify connected wallets involved in a cross-border trafficking network.
- Prevent terrorist attacks before they happen – Jihadist groups gather and communicate online to perform their attacks. These groups commonly leverage platforms such as RocketChat and Telegram to organize attacks. Law enforcement agencies can infiltrate such groups and trace their online activities to purchase travel tickets to foreign destinations and fake passports, and halt their attack before it happens.
- Identify infrastructure vulnerabilities – Law enforcement agencies utilize specialized internet of things (IoT) search engines like Shodan and Censys to discover exposed critical infrastructure systems before malicious actors exploit them.
The landscape of cybercrime continually evolves, presenting law enforcement with unprecedented challenges that require innovative approaches. OSINT stands at the forefront of these efforts, providing cost-effective and efficient methods to gather critical intelligence without the need for specialized equipment or excessive resources.
Going to the 2025 Police Security Expo?
Stop by Four Inc.’s booth #1238 to chat with the Authentic8 team and discover why Silo is the go-to digital investigations platform for law enforcement.
Silo offers several important features that make it a reliable tool for criminal investigations:
- Seamless, authentic access to social media- Silo’s Browsing Data Persistence feature securely saves session-specific data — like cookies, form-fill details and site preferences — and restores it in future sessions. Combined with Bookmark Persistence, analysts can return to platforms like Telegram without repeated logins or authentication hurdles.
- Secure 2FA with SMS inbox and anonymous email - Silo’s integrated SMS Inbox solves this by providing analysts with authentic, mainstream mobile numbers and matched email accounts. These are fully anonymized, not linked to the agency or Authentic8, and accepted by most platforms for 2FA.
- Secure use of web extensions and non-browser apps - Web extensions from the Chrome Web Store can be safely installed and managed with full admin oversight. Native mobile and third-party applications run within the same managed attribution framework, preserving identity, isolating risk, and enhancing productivity.
- Visual audit trail - In sensitive investigations, maintaining a defensible record of online activity is critical. Silos built-in session recording delivers a complete, tamper-proof audit trail of each browsing session — including every page visited, interaction made and identity used. These recordings are securely stored and indexed, allowing administrators and case leads to review sessions for validation, training or evidentiary purposes.
Silo is your all-in-one digital investigations platform to securely conduct, anonymize, manage and track digital investigations and intelligence gathering. Whether you’re investigating a suspect’s social media presence, narcotics or CSAM for sale on the dark web, or any other criminal activity threatening your community — Silo has your back.
Tags Anonymous research Law enforcement Social media

